Some common misconceptions about the Act! security alert
Written by Ken Quigley about the Act CRM Security Notice : https://www.keystroke.ca/en/blog/news/act-security-alert-2.html
Since April 19th, the date Act! made their security announcement, we’ve sent out countless email alerts and made thousands of phone calls to our customers. The reaction to these notices has been mixed, ranging from dismissive to overly alarmed. Here is a list of the five most common unexpected reactions we’ve encountered thus far:
- I only drive my Act! to church on Sundays, am I still vulnerable? Act! is not a small program that shuts down completely when you close it. Many services like SQL, Scheduler, Smart Tasks, the Web API, and the Indexing service remain running after the program is closed (ever wonder how your Outlook emails get attached to History when Act! is closed?).
Rest assured, if you’re using an unpatched or unsupported version of Act! on a computer connected to the Internet, the bots capable of exploiting this vulnerability can find you with or without Act! running. - I have nothing interesting on my PC, so no one would hack me. Bots & hackers don’t care about your data, since they’re not stealing it to sell on the open market. They only intend to sell it to one person, and that’s you by way of ransom demand. For reference, ransomware demands range from 1-5 bitcoins on average, with one bitcoin currently worth approximately $30,000 USD.
- Act! is not disclosing the details of this vulnerability, so it must be fake. Everyone loves a good conspiracy theory but consider this. Act! could announce the precise nature of this vulnerability, and paint a target on every unsupported version installed around the world. This would certainly generate more upgrade sales than the cautious “advisory” approach we’ve taken.
- My Anti-Virus software will protect me. No, it won’t. Unless it’s part of a larger security suite, a pure anti-virus program will protect you from a hack about as well as rubber boots will protect you from food poisoning.
- It won’t happen to me. We hope it doesn’t, but let’s not confuse a wish for a plan. Ransomware attacks rose 93% in 2021 compared to 2020, with 304.7 million ransomware attack attempts in the first half of that year alone. And the second half of 2021 was worse than the first.
Using software that has a known vulnerability will not keep you on the safe side of those odds.
Please don’t confuse our light tone with us taking this lightly. We were hit by ransomware in 2017, and with a team of technicians and some good luck, we managed to avoid the worst, but it was an experience we wouldn’t wish on anyone.
OK, you have my attention, what should I do?
If you have Act! Pro or Premium installed on any of your computers, we recommend taking one of the following actions:
- If the version you’re using is Act! v22.1 or newer, please visit this LINK after for a patch to secure your installation at no cost. It takes 2-3 minutes to download and apply.
- If it is an older version, and you no longer need to reference the data, please uninstall Act!, forthwith.
- If you do need ongoing access to the data, you can either disable Internet access on that workstation(s), or purchase Act! Pro v24 for a low one-time cost (limit of 5-users).
- If you have a perpetual license of an unsupported version deployed in a production environment (Act! v21 or older), we strongly recommend subscribing to Act! Premium and updating your software to a supported version, especially while Act! is running its Winback promo.
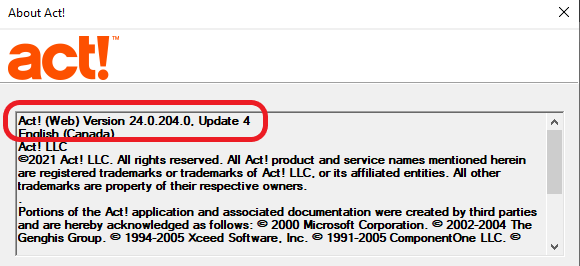
How can I tell which version of Act! I’m using? From within Act!, click Help > About Act!, and read the top line of text.